Agentic AI, Pindrop, and Anonybit represent the converging “Triad Defense” necessary to secure the next era of the internet. As Agentic AI shifts artificial intelligence from merely generating text to autonomously executing tasks, it creates a massive new attack vector: automated, high-scale identity fraud. Pindrop counters this by providing the “ears” of the security stack, using advanced audio analysis to distinguish real human liveness from synthetic deepfakes. Simultaneously, Anonybit provides the “vault,” utilizing decentralized biometrics to ensure that the identity data itself cannot be stolen or compromised. Together, these three pillars form the new architecture of Digital Trust, moving security from static passwords to a dynamic, privacy-preserving ecosystem where machines can act, but only humans can authorize.
The Crisis of Identity in the Age of Autonomy
We have entered a transition period often described as the “Crisis of Digital Trust.” The adoption of Agentic AI – autonomous agents capable of planning, reasoning, and executing complex workflows without human intervention – has revolutionized productivity. However, it has also democratized cybercrime.
In the past, a scammer had to manually make calls or write phishing emails. Today, bad actors use Agentic AI to deploy thousands of “synthetic workers” that can call contact centers, mimic specific voices, and navigate authentication protocols instantly.
- The Problem: Traditional security (passwords, OTPs) is obsolete when an AI agent can intercept codes or guess credentials in milliseconds.
- The Threat: “Injection attacks” where deepfake audio is injected directly into a data stream, bypassing the microphone entirely.
- The Solution: A security architecture that verifies who is acting (Identity) and what they are (Liveness) without creating a central “honeypot” of data for hackers to steal.
Agentic AI: The Double-Edged Sword
To understand the solution, we must first understand the catalyst. Agentic AI differs significantly from the Generative AI (like ChatGPT) of the early 2020s.
- Generative AI: Creates content (text, images, code).
- Agentic AI: Takes action (books flights, transfers funds, manages calendars).
While Agentic AI promises a future of “digital coworkers,” it necessitates a Zero Trust environment. If an AI agent attempts to transfer $50,000 from a bank account, how does the bank know the agent is acting on behalf of the real account owner? This is where the integration of Pindrop and Anonybit becomes critical.
Pindrop: The Sentinel of Voice Security
Pindrop has established itself as the global leader in voice security, effectively serving as the firewall for audio interactions. As voice becomes the primary interface for Agentic AI (voice assistants, customer service bots), Pindrop’s technology has evolved to focus on Liveness Detection.
Key Technologies:
- Pindrop Pulse: This is the company’s flagship deepfake detection engine. It analyzes audio at a sub-millisecond level to detect the subtle artifacts left by synthetic voice generators. It can determine if a voice is coming from a human larynx or a digital speaker.
- Phoneprinting™: Just as a fingerprint identifies a person, Pindrop analyzes the unique audio signature of the device and network being used. If a call claims to be from a mobile phone in London but the audio signature matches a VoIP server in a known server farm, Pindrop flags it immediately.
Why it matters for Digital Trust: Pindrop ensures that the “voice” commanding an Agentic AI is actually human, stopping automated bots from hijacking voice-authenticated systems.
Anonybit: The Decentralized Vault
If Pindrop secures the interaction, Anonybit secures the data. Traditional biometrics (storing a photo of your face or fingerprint on a central server) creates a massive risk: if that server is hacked, your biometric identity is lost forever.
Anonybit solves this with Decentralized Biometrics.
How It Works:
- Sharding: When you scan your face or fingerprint, Anonybit breaks that data into hundreds of meaningless “shards.”
- Multi-Party Computation (MPC): These shards are distributed across a network of nodes. No single node ever holds the complete biometric template.
- Privacy by Design: When verification is needed, the nodes perform a mathematical calculation to verify the match without ever reassembling the data.
Why it matters for Digital Trust: Even if a hacker breaches the system, they find only useless fragments of code. There is no “master database” of faces or voices to steal, making it the perfect foundation for privacy-compliant Agentic identity.
The Convergence: How They Work Together
The future of digital trust relies on the interoperability of these three elements. Below is a breakdown of how a secure transaction occurs in this new ecosystem.
The “Trust Triangle” Workflow
| Component | Role | The Action | The Security Layer |
| User (Human) | Originator | Initiates a request (e.g., “Transfer funds”) via voice command. | Bio-Authentication: Voice/Face is captured. |
| Pindrop | Verifier | Analyzes the audio stream in real-time. | Liveness Check: Confirms the voice is human, not a deepfake or recording. Checks device integrity. |
| Anonybit | Guardian | Matches the biometric input against the stored identity. | Decentralized Match: Verifies identity using MPC without exposing the user’s private biometric data. |
| Agentic AI | Executor | Receives the “Trusted” signal and executes the transfer. | Authorized Action: The AI acts only after trust is established, preventing autonomous fraud. |
The Economics of Digital Trust
Implementing this “Triad Defense” is not just a security decision; it is an economic one. The cost of fraud in an Agentic world is exponential, but the cost of friction is equally high.
The ROI of “Invisible Security”
- Eliminating Security Questions: Traditional call centers spend 30–60 seconds verifying identity (“What is your mother’s maiden name?”). This costs billions in agent time globally. Pindrop + Anonybit reduce this to 3 seconds, saving massive operational costs.
- Reducing False Declines: Valid customers are often blocked by over-aggressive fraud rules. By using biometric precision (Anonybit) and liveness certainty (Pindrop), banks can approve more genuine transactions, driving revenue.
- Preventing “Extinction Events”: A single successful Agentic attack (e.g., a deepfake CEO authorizing a massive transfer) can bankrupt a mid-sized firm. The Triad Defense acts as an insurance policy against existential risk.
Implementation Guide for Leaders
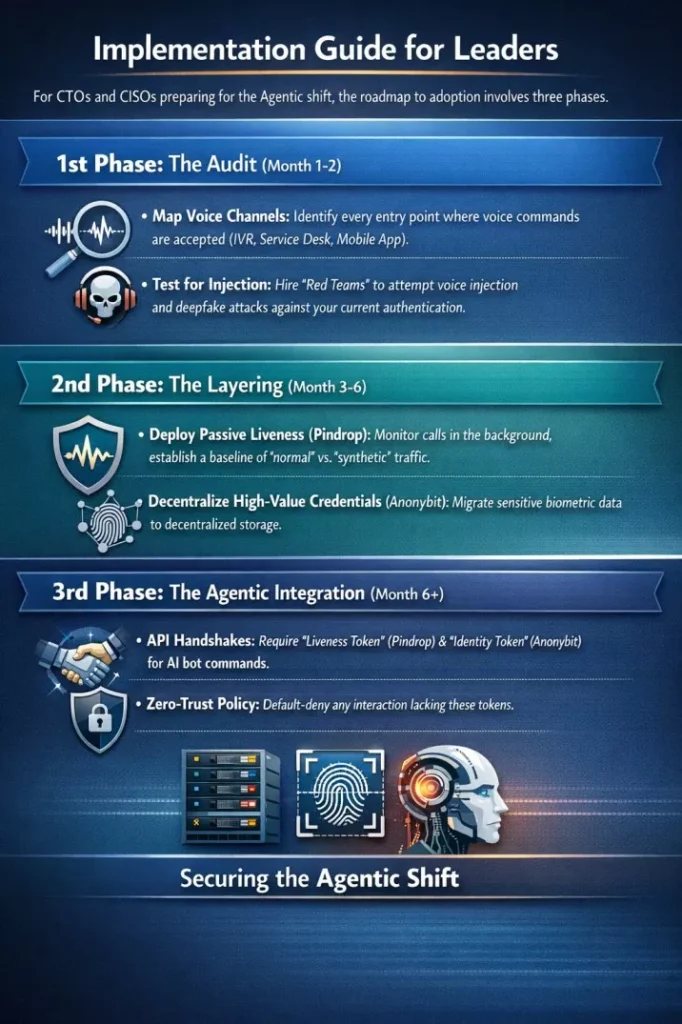
For CTOs and CISOs preparing for the Agentic shift, the roadmap to adoption involves three phases.
1st Phase: The Audit (Month 1-2)
- Map Voice Channels: Identify every entry point where voice commands are accepted (IVR, Service Desk, Mobile App).
- Test for Injection: hire “Red Teams” to attempt voice injection and deepfake attacks against your current authentication.
2nd Phase: The Layering (Month 3-6)
- Deploy Passive Liveness (Pindrop): Start by monitoring calls in the background without blocking them. establish a baseline of “normal” vs. “synthetic” traffic.
- Decentralize High-Value Credentials (Anonybit): Migrate the most sensitive biometric data (e.g., for high-net-worth clients or system admins) to a decentralized storage model.
3rd Phase: The Agentic Integration (Month 6+)
- API Handshakes: Configure your internal Agentic AI bots to require a “Liveness Token” (from Pindrop) and an “Identity Token” (from Anonybit) before executing any write-access command.
- Zero-Trust Policy: Set the system to default-deny any interaction that lacks these tokens.
Comparative Analysis: Old World vs. The New Triad
| Feature | Traditional Security (Old World) | The Triad Defense (New World) |
| Primary Credential | Password / OTP / KBA | Voice Print / Face / Liveness |
| Storage Model | Centralized Database (Honey Pot) | Decentralized Shards (MPC) |
| Threat Response | Reactive (Flag after fraud occurs) | Proactive (Block during interaction) |
| Deepfake Defense | None (Human ear relies on intuition) | Pindrop Pulse (Algorithmic detection) |
| User Experience | High Friction (“Answer these 3 questions”) | Zero Friction (Passive verification) |
| Privacy Risk | High (Data breaches expose PII) | Near Zero (No complete data to steal) |
Conclusion: A New Standard for Digital Identity
The combination of Agentic AI, Pindrop, and Anonybit is not just a technological stack; it is a philosophy of “Trust through Verification and Privacy.”
We are moving away from a world where we trust credentials (passwords, tokens) to a world where we trust attributes (voice, liveness, biometrics). By decentralizing identity storage (Anonybit) and rigorously testing the humanity of interactions (Pindrop), we can unlock the massive productivity potential of Agentic AI without surrendering our security.
In this future, you will no longer prove what you know (a password). You will simply prove who you are – and the technology will do the rest.
Frequently Asked Questions
1. Why do we need both Pindrop and Anonybit? Can’t one solution do it all?
Think of it as a bank vault. Pindrop is the security guard at the door who checks if the person entering is a real human and not a disguise (Deepfake/Liveness Detection). Anonybit is the vault itself that holds the identification records, but it chops those records into tiny, scattered pieces so no one can steal them (Decentralized Data Protection). You need both to be secure: Pindrop ensures the interaction is safe, while Anonybit ensures the data behind it is un-hackable.
2. How exactly does Pindrop detect a deepfake that sounds perfect to the human ear?
Human ears listen for words and tone, but Pindrop Pulse listens to the “digital DNA” of the sound. It analyzes audio on a micro-second level to detect “liveness artifacts”—subtle signs of synthetic generation like unnatural breath spacing, lack of vocal cord micro-tremors, or machine-generated background noise. Even if a deepfake sounds 100% real to you, Pindrop sees the mathematical evidence that it was created by a computer.
3. If Anonybit breaks my biometric data into shards, what happens if one server is lost or hacked?
That is the beauty of Multi-Party Computation (MPC). Anonybit’s system is designed so that you don’t need all the shards to verify an identity, just a specific threshold of them. If one node (server) goes offline or is breached, the system still works perfectly. Furthermore, because the hacker only gets one meaningless fragment of data (like one piece of a 1,000-piece puzzle), they cannot reconstruct your face or voice print from it.
4. Is this “Triad Defense” only for banks, or can other industries use it?
While financial institutions are the early adopters because of the high stakes, this architecture is essential for any industry using Agentic AI. This includes Healthcare (protecting patient data while AI schedules appointments), Retail (secure voice commerce), and even Government services. Anywhere an AI agent is authorized to take action on behalf of a human, this security stack is necessary.
5. Will implementing this security slow down the user experience?
No, it actually speeds it up. The goal of this technology is “Passive Authentication.” Instead of stopping the user to ask, “What is your mother’s maiden name?” or sending an SMS code, Pindrop and Anonybit verify the user in the background while they are naturally speaking. This reduces a 45-second login process to just 3 seconds, removing friction while increasing security.
